The National Security Agency (NSA) has released guidance to help organizations eliminate weak encryption protocols, which are currently being exploited by threat actors to decrypt sensitive data.
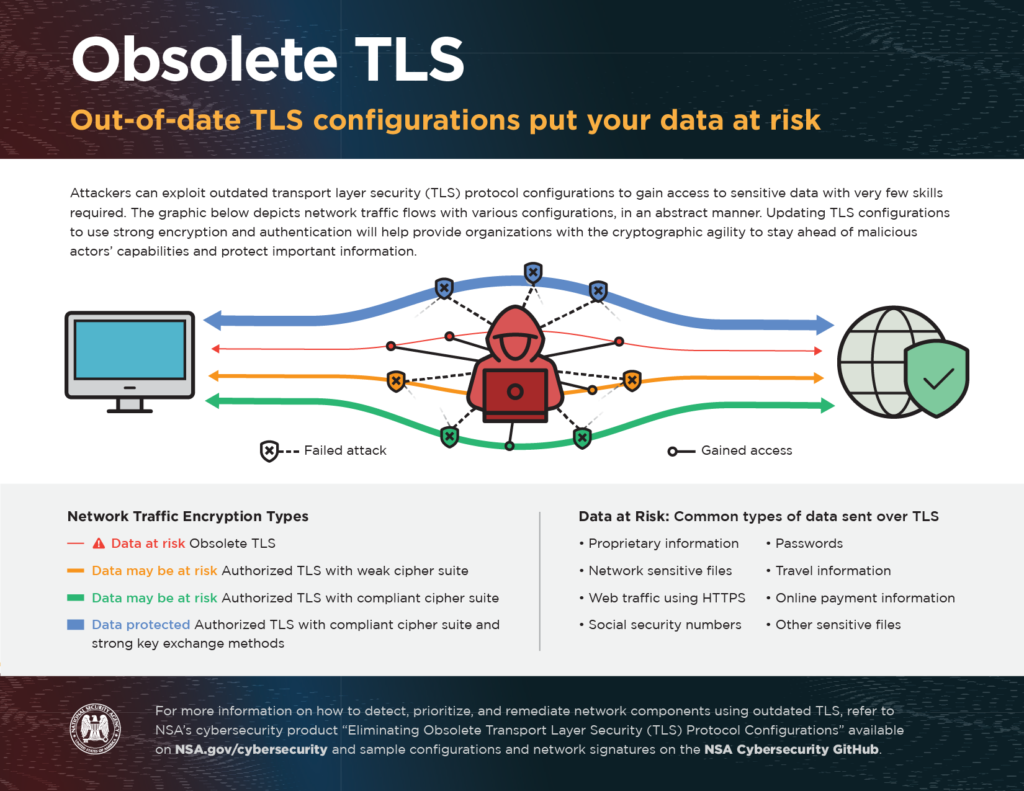
Transport Layer Security (TLS) and Secure Sockets Layer (SSL) protocols were developed to create protected channels using encryption and authentication to ensure the security of sensitive data between a server and a client. The algorithms used by these protocols to encrypt data have since been updated to improve the strength of encryption, but obsolete protocol configurations are still in use. New attacks have been developed that exploit weak encryption and authentication protocols, which are being actively used by threat actors to decrypt and obtain sensitive data.
The NSA explains that most products that use obsolete TLS versions, cipher suites, and key exchange methods have been updated, but implementations have often not kept up and continued use of these out-of-date TLS configurations carries an elevated risk of exploitation. Continued use of outdated protocols provides a false sense of security, as while data transmissions are protected, the level of protection provided is insufficient to prevent decryption of data by nation state actors and other well-resourced threat actors.
The new NSA guidance explains how to detect outdated TLS and SSL configurations, replace them with newer, more secure versions, and block obsolete TLS versions, cipher suites, and key exchange methods.
The guidance is primarily aimed at cybersecurity leaders in the National Security System (NSS), Department of Defense (DoD), and Defense Industrial Base (DIB), but can be used by all network owners and operators to better secure sensitive data.
The NSA recommends updating SSL 2.0, SSL 3.0, TLS 1.0 and TLS 1.1 and only using TLS 1.2 or TLS 1.3. The guidance included detailed information on the tools, network signatures, and server configurations necessary to only allow strong encryption protocol configurations.
“Obsolete configurations provide adversaries access to sensitive operational traffic using a variety of techniques, such as passive decryption and modification of traffic through man-in-the-middle attacks,” said the NSA in the guidance. “To help system administrators fix their network components, NSA developed several server configurations and network signatures to accompany the report that are available on the NSA Cybersecurity Github.”
Updating TLS configurations will ensure that government agencies and enterprise organizations have stronger encryption and authentication and will better protect sensitive data.
The post NSA Releases Guidance on Eliminating Weak Encryption Protocols appeared first on HIPAA Journal.