The Health Information Sharing and Analysis Center (H-ISAC) has published a framework for CISOs to manage identity and defend their organization against identity-based cyberattacks. This is the second white paper to be published by H-ISAC covering the identity-centric approach to security. The first white paper explains why an identity-centric approach to cybersecurity is now needed, with the latest white paper detailing how that approach can be implemented.
By adopting the framework, CISOs will be able to manage the full identity lifecycle of employees, patients, practitioners, and business partners in a way that guards against cyberattacks on identity, lowers risk, and increases operational efficiencies.
The framework has been developed for CISOs at healthcare organizations of all sizes. As such, it does not offer a one-size-fits-all approach. Instead, components of the framework can be applied differently based on different environments and use cases. CISOs will need to assess the resources available and their unique risks and decide how best to apply the framework.
The framework details the different components that are required in a modern identity-centric approach to cybersecurity and outlines how those components integrate and inter-relate to secure the enterprise.
Source: H-ISAC
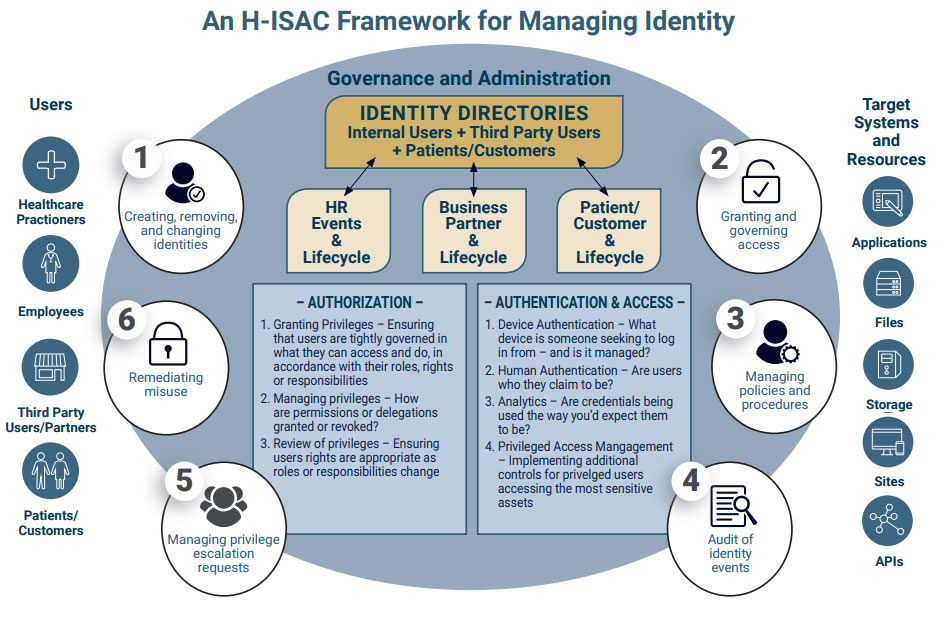
The central concept of the framework is simple. How to allow users to access resources in a way that protects against cyberattack. At the heart of the framework is an identity governance and administration system, which serves as the central nervous system that ties in all the other components and ensures they work seamlessly together.
The identity governance and administration system allows organizations to establish set rules and processes related to the creation, removal, and updating of accounts, manage policies and processes of all aspects of their identity and access management (IAM) system, manage privilege escalation requests, conduct audits for compliance purposes, and take actions to remediate any misuses of the IAM system.
The framework uses identity directories as an authoritative identity store for an organization, which detail roles, accounts, attributes, and the privileges associated with different roles and accounts. The white paper details three guiding principles for authorization: Granting privileges, managing privileges, and reviewing privileges. Privileges must be tightly controlled and assigned based on roles, rights, and responsibilities. Processes must be defined to manage privileges and update them as circumstances change. Reviews should also be conducted to ensure that users have only been assigned rights that are appropriate for their role and responsibilities.
A few years ago, all that was required to gain access to resources was a password, but threat actors are now adept at stealing passwords and as a result the security utility of passwords has diminished. H-ISAC therefore recommends multi-factor authentication. The framework takes MFA one step further and includes device authentication, human authentication, analytics, and privileged access management to enable continuous, risk-based authentication.
Device authentication ensures only trusted devices are granted access to resources. Human authentication is then required to ensure that the correct person is using that device. Analytics are then used to identify anomalies that could indicate attempts by unauthorized individuals to access resources, such as a device being used to access resources from California and then five minutes later being used in New York. Privileged access management solutions should also be used for session monitoring and to implement additional layers of authentication to prevent credential compromise and limit privilege escalation.
The framework also outlines four different use cases: On-boarding new employees, managing users and changing privileges when an employee’s role changes, credentialing a third-party business partner for limited systems access, and credentialing new patients.
The post H-ISAC Publishes Framework for Managing Identity in Healthcare appeared first on HIPAA Journal.