Microsoft has discovered a large-scale spear phishing campaign being conducted by the Russian Advanced Persistent Threat (APT) group behind the SolarWinds Orion supply chain attack.
The spear phishing campaign has been active since at least January 2021 and the APT group, tracked by Microsoft as Nobelium. The APT group has been experimenting and has trialed various delivery techniques, including leveraging the Google Firebase platform to deliver a malicious ISO file via HTML email attachments that deliver a variety of malware payloads.
Nobelium escalated the campaign on May 25, 2021 when it started using the Constant Contact mass-mailing service to distribute messages to targets in a wide range of industry verticals. The latest campaign targeted around 7,000 individual accounts across 350 government organizations, intergovernmental organizations and nongovernmental organizations. Each target had its own unique infrastructure and tooling, which has helped the group stay under the radar.
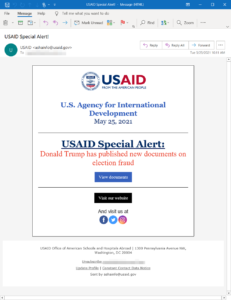
The attackers gained access to the Constant Contact account of the U.S. Agency for International Development (USAID) and delivered spear phishing messages under the guise of a USAID Special Alert. The messages have a reply-to address on the usaid.gov domain and were sent from the in.constantcontact.com domain.
The messages claimed “Donald Trump has published new documents on election fraud”, with the messages including a button to click to view the documents. If the recipient clicks the link in the email, they are directed to the legitimate Constant Contact service, and then redirected to a URL under the control of Nobelium that delivers a malicious ISO file. Within the ISO file are a decoy document, a .lnk shortcut that executes a Cobalt Strike Beacon loader, and a malicious DLL file that is a Cobalt Strike Beacon loader and backdoor dubbed NativeZone by Microsoft.
Once the payloads are deployed, Nobelium gains persistent access to compromised systems and can subsequently complete further objectives such as lateral movement, data exfiltration, and the delivery of additional malware.
A previous campaign in May also used the combination of HTML and ISO files, which dropped a .NET first-stage implant – TrojanDownloader:MSIL/BoomBox – that was used for reconnaissance and to download additional malicious payloads from Dropbox.
The phishing campaign is being investigated by the Cybersecurity and Infrastructure Security Agency (CISA) and the Federal Bureau of Investigation (FBI). Constant Contact issued a statement confirming that the account credentials of one of its customers were compromised. “This is an isolated incident, and we have temporarily disabled the impacted accounts while we work in cooperation with our customer, who is working with law enforcement,” said Constant Contact.
The U.S. Department of Justice announced on Friday it obtained court orders and was able to seize two domains used by the attackers for file exfiltration and to communicate with malware on compromised networks: theyardservice[dot]com and worldhomeoutlet[dot]com.
Microsoft has warned that the tactics, techniques, and procedures used by Nobelium have had a high rate of evolution. “It is anticipated that additional activity may be carried out by the group using an evolving set of tactics,” warned Microsoft.
Microsoft has published Indicators of Compromise (IoCs) and has suggested several mitigations that can reduce the impact of this threat, including the use of antivirus software, enabling network protection to prevent applications or users from accessing malicious domains, and implementing multi-factor authentication to prevent the use of compromised credentials.
The post SolarWinds Orion Hackers Targeting U.S. Organizations with New Spear Phishing Campaign appeared first on HIPAA Journal.