An audit of the Department of Health and Human Services conducted for the HHS’ Office of Inspector General (OIG) to assess compliance with the Federal Information Security Modernization Act of 2014 (FISMA) in the fiscal year 2021 has seen the agency’s security program rated ‘not effective’, as was the case in fiscal years 2018, 2019, and 2020. The audit was conducted at five of the 12 operating divisions of the HHS, although OIG did not state which five divisions were audited.
In order to receive an effective rating, the HHS is required to reach the ‘Managed and Measurable’ maturity level for the Identify, Protect, Detect, Respond, and Recover function areas, as required by DHS guidance and the FY 2021 Inspector General FISMA Reporting Metrics.
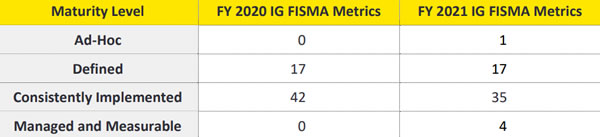
OIG said in the report that the HHS has continued to make changes to strengthen the maturity of its enterprise-wide cybersecurity program and is making progress to sustain cybersecurity across all FISMA domains. The HHS security program strengthened the maturity of controls for several individual FISMA metrics, although progress in some areas has not been made due to the lack of full implementation of Information Security Continuous Monitoring (ISCM) efforts across its operating divisions. This is critical as reliable data and metrics are required to make informed risk management decisions.
The HHS has partially implemented its Continuous Diagnostics and Mitigation (CDM) strategy, which has improved visibility into some assets, and awareness of vulnerabilities and threat information has improved through the use of RSA Archer and Splunk. Progress has been made toward implementing a full department-wide CDM program to ensure continuous monitoring of HHS networks and systems, provide real-time reporting of operating divisions’ status and progress to address and implement strategies to combat risk, prioritize issues using established risk criteria, and improve its cybersecurity response capabilities.
The HHS has advanced its implementation of CDM tools and processes but does not have a definitive schedule for fully implementing the CDM program across all operating divisions. Until the HHS fully implements its CDM strategy, the HHS may not be possible to identify cybersecurity risks on an ongoing basis, prioritize efforts to address risks based on their potential impacts and be able to mitigate the most significant vulnerabilities first.
OIG has made several recommendations for improving the maturity of the HHS information security program. The HHS should continue with its implementation of an automated CDM solution to provide a centralized, enterprise-wide view of risks across all of HHS. The ISCM strategy needs to be updated to include a more specific roadmap, with target dates specified for ISCM deployment across all HHS operating divisions. An enterprise risk assessment over known control weaknesses should be performed and an appropriate risk response must be documented, and the HHS needs to develop a process to monitor information system contingency plans to ensure they are developed, maintained, and integrated with other continuity requirements by information systems. The HHS concurred with all OIG recommendations.
The post HHS Information Security Program Rated ‘Not Effective’ appeared first on HIPAA Journal.