13 vulnerabilities have been identified in the Siemens Nucleus RTOS TCP/IP stack that could potentially be exploited remotely by threat actors to achieve arbitrary code execution, conduct a denial-of-service attack, and obtain sensitive information.
The vulnerabilities, dubbed NUCLEUS:13, affect the TCP/IP stack and related FTP and TFTP services of the networking component (Nucleus NET) of the Nucleus Real-Time Operating System (RTOS), which is used in many safety-critical devices. In healthcare, Nucleus is used in medical devices such as anesthesia machines and patient monitors.
One critical vulnerability has been identified that allows remote code execution which has a CVSS v3 severity score of 9.8 out of 10. Ten of the vulnerabilities are rated high severity flaws, with CVSS scores ranging from 7.1 to 8.8. There are also two medium-severity flaws with CVSS scores of 6.5 and 5.3.
The vulnerabilities were identified by security researchers at Forescout Research Labs, with assistance provided by researchers at Medigate.
The vulnerabilities affect the following Nucleus RTOS products:
- Capital VSTAR: All versions
- Nucleus NET: All versions
- Nucleus ReadyStart v3: All versions prior to v2017.02.4
- Nucleus ReadyStart v4: All versions prior to v4.1.1
- Nucleus Source Code: All versions
Identifying where vulnerable code has been used is a challenge. The researchers attempted to estimate the impact of the vulnerabilities based on evidence collected from the official nucleus website, the Shodan search engine, and the Forescout device cloud. Healthcare is the worst affected industry, with 2,233 vulnerable devices. 1,066 government devices were identified as vulnerable, with other vulnerable devices found in retail (348), financial (326), manufacturing (317), with 1,176 vulnerable devices found in other industry sectors. 76% of the vulnerable devices are used for building automation, 13% are used in operational technology, 4% for networking, 5% IoT, and 2% were computers running Nucleus.
The vulnerabilities were reported to Siemens under responsible disclosure guidelines and Siemens has made patches available to fix all of the identified vulnerabilities. Siemens said some of the flaws had been identified and addressed in previously released versions, but no CVEs were issued.
Applying patches to fix the vulnerabilities can be a challenge, especially for embedded devices and those of a mission-critical nature, such as devices used in healthcare settings.
If patches cannot be applied, Forescout and Siemens recommend implementing mitigating measures to reduce the potential for exploitation. Siemens recommends protecting network access to devices with appropriate mechanisms and ensuring the devices operate within protected IT environments that have been configured in accordance with Siemens’ operational guidelines.
Forescout has released an open-source script that uses active fingerprinting to detect devices running Nucleus for discovery and inventory purposes. After identifying devices, Forescout recommends enforcing segmentation controls and practicing proper network hygiene, including restricting external communication paths and isolating or containing vulnerable devices in zones until they can be patched.
In addition, all network traffic should be monitored for malicious traffic and progressive patches released by vendors of affected devices should be monitored. A remediation plan should be developed for all vulnerable assets that balances risk with business continuity requirements.
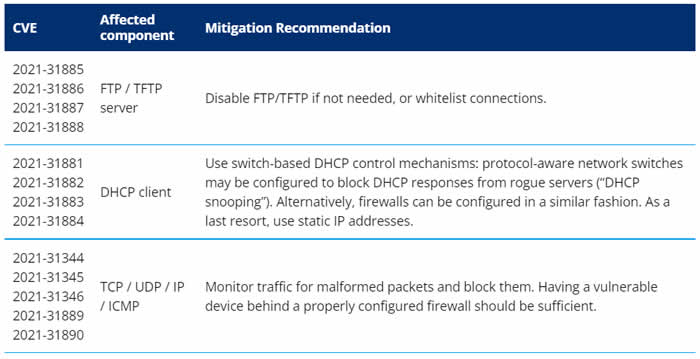
Specific mitigations recommended by Forescout are detailed in the table below:
The post Medical Devices Affected by 13 Siemens Nucleus RTOS TCP/IP Stack Vulnerabilities appeared first on HIPAA Journal.