A warning has been issued to the healthcare and public health (HPH) sector about an ongoing Monkeypox phishing campaign targeting U.S. healthcare providers that attempts to steal Outlook, Office 365, and other email credentials.
Monkeypox is a highly contagious viral disease caused by a virus from the same family as smallpox. According to the Centers for Disease Control and Prevention (CDC), there have been almost 66,000 cases diagnosed globally in the current outbreak, and more than 25,100 cases in the United States. California, New York, Florida, Texas, and Georgia are the worst affected states, with the cases mostly confined to the LBGTQ+ community.
Malicious actors often piggyback on major news stories and use these themes to conduct convincing phishing campaigns. Campaigns using monkeypox lures were therefore inevitable, and they are likely to continue and increase in line with the rising numbers of cases. Monkeypox and COVID-19-related phishing campaigns have a high success rate as there is considerable interest in the outbreak and concern about infections.
The Health Sector Cybersecurity Coordination Center (HC3) warns that these emails may be sent from the email account of an HPH-related entity that has previously been compromised, or from a non-HPH-related entity. When a phishing email is sent from a trusted email account it increases the probability of the email being opened.
The emails claim to offer important information about the current monkeypox outbreak in the United States and have the subject line, “Data from (Victim Organization Abbreviation): “Important read about -Monkey Pox– (Victim Organization) (Reference Number).” The message body includes the text, “Please see the attached important read about “Monkey Pox” for your reference. It is a good read; thought I’d share with you. Stay safe.”
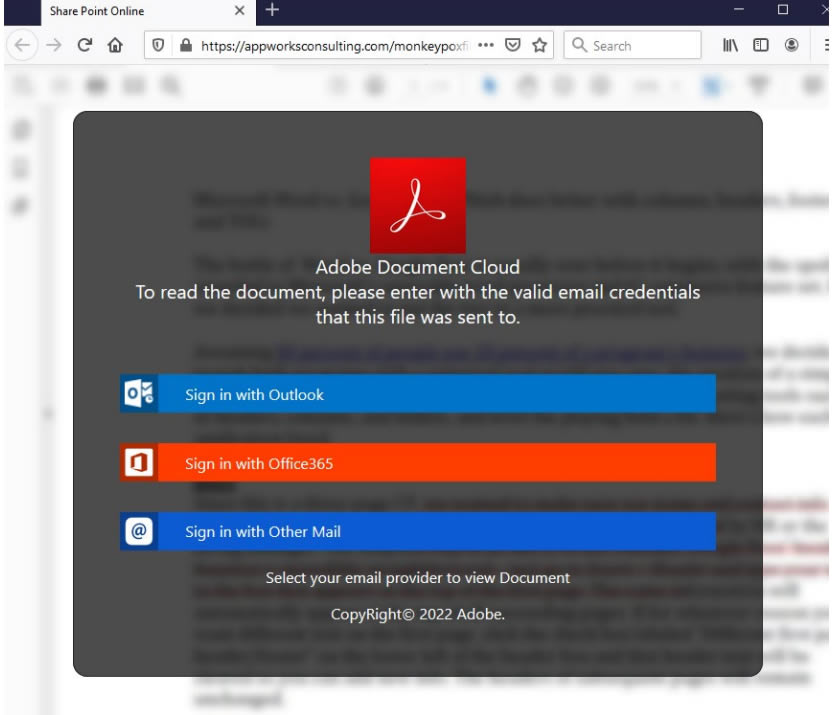
The emails have a PDF file attachment named, “MPV Update_070722F.pdf” although other names may also be used. The attached file includes a malicious hyperlink that directs the recipient to a Lark Docs site, which has an Adobe Cloud theme and offers a secure fax document from Xerox Scanner to download. If the user attempts to download the file they will be directed to another website, where the user is told they must enter their valid email credentials in order to view the file. If those credentials are entered, they will be harvested and used by the threat actor to remotely access the user’s email account.
In addition to raising awareness of the monkeypox phishing campaign, healthcare organizations should be providing regular security awareness training to the workforce covering security best practices, such as the importance of setting long, complex passwords for all accounts, not clicking links or opening attachments in unsolicited emails, and to only download files from trusted publishers. Security awareness training should cover the phishing and social engineering techniques commonly used by threat actors, and it is recommended to also conduct phishing simulations on the workforce. Phishing simulations have been proven to significantly reduce susceptibility to phishing attempts.
Some employees will still click links and open attachments even with training, so it is important to ensure that technical measures are implemented to protect against phishing, such as spam filters to block phishing emails, web filters to block malicious websites, and multifactor authentication for email accounts to prevent unauthorized access to accounts using stolen credentials.
The post Monkeypox Phishing Campaign Targets Healthcare Providers appeared first on HIPAA Journal.