The National Security Agency (NSA) has recently released new guidance to help organizations adopt a Zero Trust approach to cybersecurity to better defend against increasingly sophisticated cyber threats.
Zero Trust is a security strategy which assumes that breaches are inevitable or have happened and an intruder is already inside the network. This approach assumes that any device or connection may have been compromised so it cannot be implicitly trusted. Continuous verification is required in real time from multiple sources before access is granted and for system responses.
Adopting a Zero Trust approach to security means adhering to the concept of least-privileged access for every access decision and constantly limiting access to what is needed, with anomalous and potentially malicious activity constantly examined.
“Zero Trust is a security model, a set of system design principles, and a coordinated cybersecurity and system management strategy based on an acknowledgement that threats exist both inside and outside traditional network boundaries,” explained the NSA in the guidance. “Zero Trust repeatedly questions the premise that users, devices, and network components should be implicitly trusted based on their location within the network.”
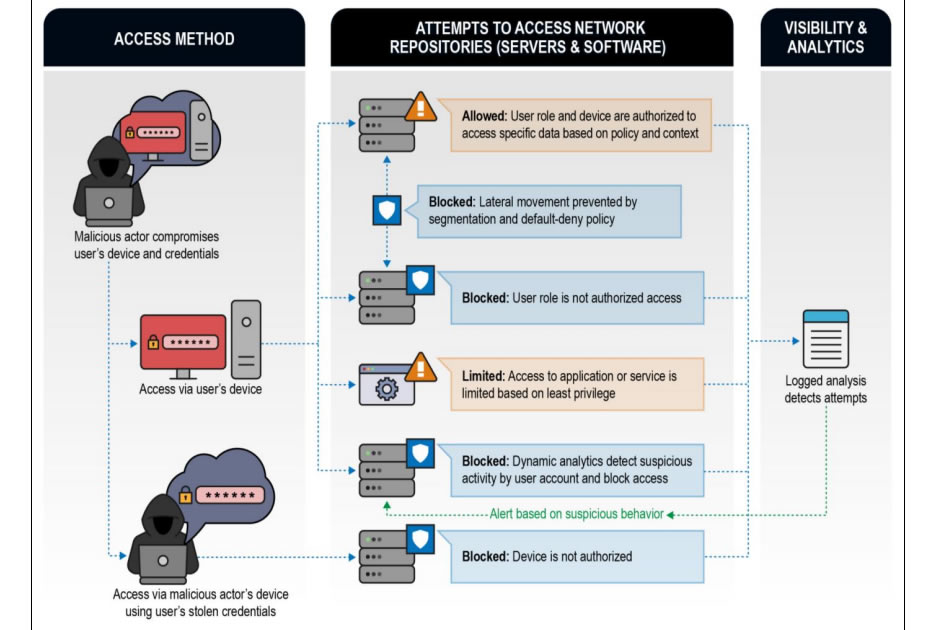
The Zero Trust approach provides far greater security against external threat actors and authorized insiders with malicious intentions. When an authorized user or remote cyber attacker uses credentials to gain access to resources, those credentials and the device used are assumed to be malicious until proven otherwise. Sine access to networks and resources is limited, and networks are segmented, the potential harm that can be caused is severely reduced and lateral movement is restricted.
Traditionally, cybersecurity has been focused on protecting internal networks from external threats. Provided the network perimeter is not breached, this approach is effective, but today’s increasingly sophisticated cyber threats often breach the perimeter defenses, after which threat actors are able to move laterally within networks undetected, as occurred in the SolarWinds supply chain attack. A Zero trust approach to security would not prevent a system breach, but the harm caused would be drastically reduced and alerts would be generated to advise network defenders of a potential attack in progress.
The NSA provides examples in the guidance of how the Zero Trust approach blocks attempts by a threat actor using a legitimate user’s stolen credentials to access network resources using their own or the user’s device.
The Zero Trust approach is also effective at blocking supply chain attacks, when a threat actor adds malicious code to a device or application. In these attacks, communication between the device or app and the attacker would not be possible as the compromised device or app would not be trusted.
The transition to this new approach to security requires security teams to adopt a Zero Trust mindset which requires coordinated and aggressive system monitoring, system management, and defensive operations capabilities. All requests for access to critical resources, network traffic, devices and infrastructure must be assumed to be malicious, and acceptance that access approvals to critical resources incur risk, therefore security teams must be prepared to perform rapid damage assessment, control, and recovery operations.
Adopting a Zero Trust approach to security requires major changes to existing information systems and considerable time and effort, and there are likely to be many challenges. Fortunately, the change to Zero Trust can be implemented in stages starting with fundamental integrated capabilities, then refining capability integration and further refining capabilities, before deploying advanced protections and controls with robust analytics and orchestration. When Zero Trust functionality is introduced incrementally in accordance with a strategic plan, risk will be reduced accordingly at each step.
The NSA guidance provides an outline of the Zero Trust approach to security, recommendations and best practices for transitioning to Zero Trust, resources required for a successful transition, and how the Zero Trust implementation can be matured to ensure success.
The post NSA Releases Guidance on Adopting a Zero Trust Approach to Cybersecurity appeared first on HIPAA Journal.