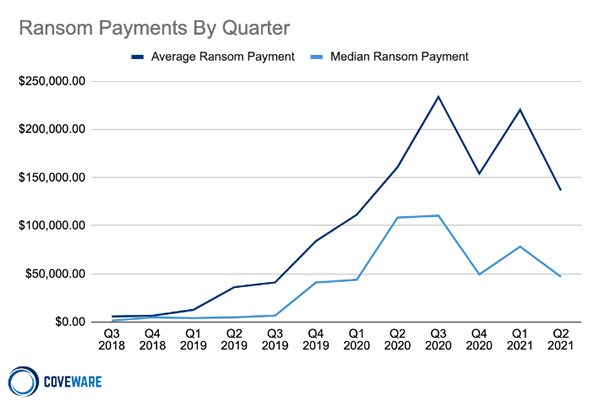
The average ransom payment made by victims of ransomware attacks fell by 38% between Q1 and Q2, 2021, according to the latest report from ransomware incident response company Coveware. In Q2, the average ransom payment was $136,576 and the median payment decreased by 40% to $47,008.
One of the key factors driving down ransom payments is a lower prevalence of attacks by two key ransomware operations, Ryuk and Clop, both of which are known for their large ransom demands. Rather than the majority of attacks being conducted by a few groups, there is now a growing number of disparate ransomware-as-a-service brands that typically demand lower ransom payments. In Q2, Sodinokibi (REvil) was the most active RaaS operation conducting 16.5% of attacks, followed by Conti V2 (14.4%), Avaddon (5.4%), Mespinoza (4.9%), and Hello Kitty (4.5%). Ryuk only accounted for 3.7% of attacks and Clop 3.3%.
The Sodinokibi gang has now gone silent following the attack on Kaseya and appears to have been shut down; however, the group has shut down operations in the past only to restart with a new ransomware variant. Even if the operators have retired, the affiliates used to conduct the attacks are likely to just switch to an alternative RaaS operation so attack volume may not be affected.
The most common vectors used in attacks has been fluctuating over the past few months. In Q1, 2021 there was an increase in brute force attacks on Remote Desktop Protocol (RDP) and the exploitation of software vulnerabilities, with phishing attacks falling. In Q2, RDP compromises and software vulnerability exploits both declined and email phishing increased, with phishing and RDP compromises now equally common. The exploitation of software vulnerabilities is the attack vector of choice for targeted attacks on large enterprises, and those attacks tend to be conducted only by the most sophisticated RaaS operations with large operating budgets that allow them to purchase single day exploits or buy access to large networks.
In Q2, more than 75% of ransomware attacks were on businesses with fewer than 1,000 employees. This is because these smaller companies are less likely to invest in security awareness training for the workforce and email security to block phishing attacks. They are also more likely to expose RDP to the Internet. Smaller businesses are also more likely to outsource security to MSPs. MSPs remain a major target, as an attack on an MSP will allow the attacker to then attack all MSP’s clients.
The report indicates a fall in the effectiveness of double extortion tactics. This is where prior to file encryption, sensitive data are exfiltrated. A demand is issued for the key to decrypt data and a second payment is required to prevent the exposure or sale of stolen data. In Q2, 81% of attacks involved data exfiltration prior to file encryption, up from 76% in Q1.
However, payment to ensure data deletion is now much less likely. In 2020, 65% of victims that were able to recover data from backups paid the attackers to prevent the exposure of stolen data, but in Q2, 2021 the percentage was just 50%.
The most attacked industry sectors in Q2 were the public sector (16.2%), professional services (13.3%), and healthcare (10.8%). Coveware suggests that these industries may not be specifically targeted, instead they are simply the easiest to attack. For instance, the number of attacks on law firms increased but that was largely down to the attack by the Clop ransomware group on Accellion File Transfer Appliances, which were disproportionately used by law firms.
Coveware reports that the average downtime from a ransomware attack declined by 15% in Q2, with victims typically having 23 days of downtime following at attack; however, this was attributed to an increase in data only attacks where there was no material business interruption.
The post The Average Ransomware Payment Fell by 38% in Q2, 2021 appeared first on HIPAA Journal.