COVID-19 has forced many organizations to rapidly scale up the numbers of employees working from home, which has created new opportunities for cybercriminals to conduct attacks. Cyberattacks on remote workers have increased substantially during the COVID-19 lockdown, with application-level protocols used by remote workers to connect to corporate systems now being extensively targeted.
Remote Desktop Protocol (RDP) is a proprietary communications protocol developed by Microsoft to allow employees, IT workers, and others to remotely connect to corporate systems, services, and virtual desktops. The protocol has been used by many organizations to allow their employees to work from home on personal computers.
RDP has also proven to be popular with cybercriminals. In line with the increase in remote workers accessing systems via RDP, cybercriminals have stepped up attacks. New data from Kaspersky show a major worldwide increase in brute force attacks on RDP.
In order to connect via RDP, employees typically need to enter a username and password. Brute force attacks on RDP are conducted to guess those passwords, which involves trying different password combinations until the right one is guessed. That can take a long time for complex passwords, but the attacks start with dictionary words and passwords obtained in prior data breaches. Annual worst passwords lists show a great deal of people still choose easy to remember passwords, which can be correctly guessed in these automated RDP attacks in a matter of seconds.
Once the credentials have been correctly guessed, they can be used to remotely connect to whatever systems an employee is authorized to access. Even if a fairly low-level set of credentials is compromised, it can give hackers the foothold in the network to conduct extensive attacks on the organization. These unauthorized logins using stolen credentials can be difficult for IT security teams to identify.
Once access is gained, attackers can take control of email accounts and send phishing emails internally to other employees. As has been made clear in the many phishing incidents reported by healthcare providers in recent months, a single email account compromise could result in a data breach involving hundreds, thousands, or even hundreds of thousands of patents’ protected health information. Ransomware and other malware can also be installed.
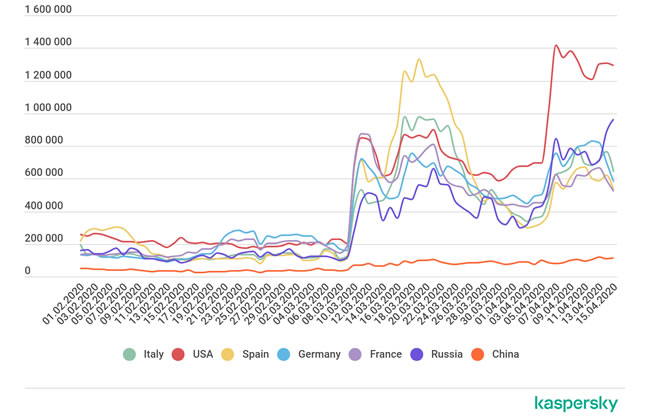
The scale of the attacks is alarming. “During the last year, there were some spikes of such attacks in different regions, but they were mainly local and small,” said, Kaspersky security researcher, Dmitry Galov. “Right now, we can see that almost worldwide, the amount of attacks increased significantly. For instance, in February we witnessed 93,102,836 attacks globally. In April, the figure was already 326,896,999.”
The number of RDP brute force attacks in the United States more than doubled between January 2 and March 3, and almost tripled by April 7, when there were 1.4 million RDP brute force attacks detected.
The brute force RDP attacks are likely to continue at high levels for the foreseeable future, and certainly until the number of remote employees reduces once the COVID-19 crisis is over.
There are several steps that companies can take to reduce the risk of these attacks succeeding. One of the most important steps to take is to implement password policies that force users to set strong passwords that are difficult to guess. Two-factor authentication is also important. If a password is guessed, a second factor must be provided before a connection is allowed. Employees should also use a corporate VPN to connect remotely along with Network Level Authentication (NLA) measures to block unauthorized access attempts. Kaspersky also warns that if RDP is not being used by remote employees, port 3389 should be disabled.
The post Worldwide Spike in Brute Force RDP Attacks During COVID-19 Pandemic appeared first on HIPAA Journal.