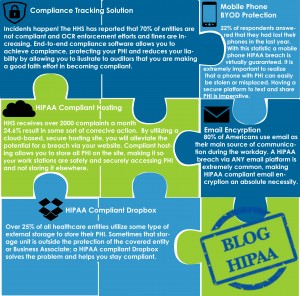
In the midst of ever-increasing HIPAA regulations and more sophisticated threats to patient information, it’s important to know how to stay safe while also being HIPAA compliant. Luckily for you, Blog HIPAA focuses on 5 great tools that help protect patient information and ease the compliance burden:
- Email encryption
- Mobile phone BYOD protection
- HIPAA compliant storage
- HIPAA compliant hosting
- Compliance tracking solution
Every company, large or small, should be doing 5 key things to become and stay HIPAA compliant.
After extensive research Blog HIPAA has found 5 vendors that focus their efforts on compliance. .
Blog HIPAA chose to highlight these vendors because their services provide a great start to achieving HIPAA compliance. Many organizations do not realize that sensitive information must be shared and stored on specific platforms. Blog HIPAA’s 5 trusted vendors can help you build out your arsenal of compliance tools.
5 Great Tools to Help Achieve HIPAA Compliance
Email Encryption:
Why? 80% of Americans use email as their main source of communication during the workday. HIPAA breaches via email are extremely common, making HIPAA compliant email encryption an absolute necessity.
DataMotion
We asked Bob Janacek, Chief Technology Officer at DataMotion to comment on why email encryption is a vital component of a HIPAA compliance strategy and what key best practices an organization should keep in mind when selecting an email encryption vendor.
The Critical Need for Email Encryption
When an email contains sensitive data, covered entities and business associates are required by regulations like HIPAA and HITECH to Secure the email. Why?
Unencrypted email messages and files hop from point to point through routes over the Internet until they reach their destination. At any of those points, data is open for scrutiny and can be copied or breached by unauthorized users. When encryption is used, data traverses the points between the sender and the recipient in a secure manner, shielded from prying eyes.
Healthcare providers and their business associates face a number of challenges in keeping up with frequently-changing data security regulations. Email encryption is an easy way to secure these sensitive communications and work towards regulatory compliance. Finding an HCP website data provider can help businesses feel more secure online and with sensitive information.
Here are some best practices to help reduce the chance of protected data from being exposed through email or file transfers.
- Keep your email encryption system simple
Employees must be able to easily do their work using security technology or they’ll turn to less-than-secure methods. Similarly, communications and information sharing between employees, associates and patients must proceed without placing any burdens on the parties involved. Ease-of-use is paramount. For example, the file-sharing feature within software like filecenterdms could be suitable should you use encryption and other products alongside to ensure compliance.
- Use Policy-based Gateway Filtering
Deploy gateway technology that can filter messages and the wide variety of file format attachments used today. To avoid false-positives and an ensuing drain on IT hours and resources, use technology that combines pattern and exact matching to specific data lists when scanning for protected data.
- Look for Exceptional Handling of File Attachments
A good approach is to use a solution that encrypts large files as email attachments, not just the email itself, maintaining compliance, control and ease of use.
- Make Use of Extensive Logging and Reporting
Look for a solution that provides extensive logging and reporting to help manage operations, as well as providing details for audits and proof of compliance.
- Require Seamless Mobile Integration
With today’s modern workforce, employees conduct a great deal of work using mobile devices. Look for an email encryption solution that works with the existing email clients of mobile devices so no separate app or complexity is needed.
As a provider of secure messaging solutions such as email encryption and Direct Secure Messaging – we are constantly engaged by providers to help them stay in compliance with expanding regulations, including HIPAA. We are an accredited Health Information Service Provider (HISP), and work with providers and hospital EHR systems – such as EPIC and MEDITECH, to integrate Direct Secure Messaging and meet Transitions of Care requirements for MU2 attestation.
Why? 22% of respondents answered that they had lost their phones in the last year. With this statistic a mobile phone HIPAA breach is virtually guaranteed. It is extremely important to realize that a phone with PHI can easily be stolen or misplaced. Having a secure platform to text and share PHI is imperative.
qliqSOFT
HIPAA compliance should be on the minds of most covered entities as breaches not only sacrifice the trust you’ve established with your patients, but also they’re extraordinarily expensive. Given what many called a banner year in healthcare data breaches, many industry professionals were happy to bid 2013 adieu. From the massive Advocate data breach to the Affinity Health Plan photocopier breach, healthcare executives finally had to face the music and tighten information security controls in a post HIPAA/HITECH Omnibus world.
To provide secure communications in an increasingly unsecure world, one must constantly engage in an open dialogue with industry experts and customers to determine how best to address efficient communication between providers, patients, and caregivers at a time where BYOD and text messaging is the norm. One way to ensure security is to cut out unnecessary cloud-based messaging hosts. Utilizing “cloud pass-thru” technology is one powerful way to minimizing the number of potential security risks.
A secure communication platform that takes into account security, HIPAA requirements, and usability will protect PHI and have the familiarity of SMS. With cloud-pass through messaging, public/private key encryption, and message archival behind the healthcare organizations’ firewall, qliqSOFT’s secure texting service provides for rich communication and minimizes the risk of a HIPAA breach and the reason it was chosen as one of the 5 pieces to solve the HIPAA compliant puzzle.
 HIPAA Compliant Storage/Dropbox:
HIPAA Compliant Storage/Dropbox:
Why? Over 25 % of all healthcare entities utilize some type of external storage to store their PHI. Dropbox is by far the most popular cloud storage and synchronization solution, but it does not offer safeguards for HIPAA compliance. A HIPAA compliant layer of encryption for Dropbox addresses HIPAA requirements and also helps your team leverage the benefits of the cloud and remain productive.
Sookasa
We caught up with Sookasa’s CEO and co-founder, Asaf Cidon, and asked him about how to maintain HIPAA compliance while using cloud storage and file sharing solutions like Dropbox.
What should healthcare professionals be aware of when adopting cloud storage solutions like Dropbox?
It’s a common misconception that signing a BAA is sufficient to maintain HIPAA compliance. A signed BAA is an important requirement but is not sufficient to guarantee that your data will be safe in the cloud-connected mobile world. For example, some cloud storage services like Egnyte offer a BAA, but they do not offer any data protection for your PHI when it is accessed on a device. Key requirements for preventing HIPAA breaches for cloud storage are:
- Encryption: encryption of files both on the cloud and on mobile devices and desktops
- Access control: Central control of who on your team can access files, even if a device is taken offline
- Audit trails: full audit trails for every file access on the cloud and on mobile
How do healthcare professionals leverage cloud storage and sharing solutions?
Sookasa’s healthcare customers use Dropbox for many different purposes. Some of them use it to synchronize files across multiple offices and devices. Many use Dropbox to access files on-the-go, for example on their iPads. Our users also utilize Dropbox to share files with other organizations, for example to send data to their medical billing provider or to send medical images to an external radiology department.
Why? HHS receives over 2000 complaints a month 24.6% result in some sort of corrective action. By utilizing a cloud-based secure hosting site, you will alleviate the potential for a breach via your website. Compliant hosting allows you to store all PHI on the site, making it so your terminals or work stations are safely and securely accessing PHI and not storing it elsewhere.
Online Tech
We caught up with Online Tech’s April Sage, Director of Healthcare IT and asked her why HIPAA compliant hosting is important and what to look for in a HIPAA compliant hosting partner.
Why is HIPAA compliant hosting important?
Healthcare applications touch and store some of the most valuable and sensitive data about a patient. Keeping patient data secure within the data center can reduce risks of having data on portable devices. In addition to making sure the data is safe, patient data must be available at the point-of-care. If your organization focuses on delivering healthcare applications but doesn’t want the burden of maintaining server infrastructure, look for a hosting provider that embraces and delivers on their responsibility to protect patient data.
What should we look for in a HIPAA compliant hosting partner?
In addition to making sure the hosting provider can meet your technical specifications, make sure to look beyond the technology. Key things to look for include:
- Will they sign a Business Associate Agreement (BAA)?
- Have they been independently audited against the HHS OCR HIPAA audit protocol?
- Will they share documentation of the audit with the auditor’s opinion of compliance?
- Do their people, processes, and technology align to demonstrate a culture of compliance? Don’t underestimate the importance of an on-site visit to see for yourself where your patient data will reside.
Why? Incidents happen! HHS has reported that 70% of entities are not compliant OCR enforcement efforts and fines are increasing. End-to-end compliance software allows you to achieve compliance, protecting your PHI and reduces your liability by allowing you to illustrate to auditors that you are making a good faith effort in regard to being compliant.
Compliancy Group
We reached out to Bob Grant, former HIPAA auditor and Chief Compliance Officer of the Compliancy Group, and asked his opinion on using software to track and maintain your HIPAA compliance due to the ever changing regulations and compliance challenges that are placed on everyone from a front desk manager to an experienced compliance officer.
Why is a compliance tracking solution necessary in today’s world?
With OCR enforcement and fine efforts on the rise, a need for an end-to-end compliance solution is ever increasing. Protection of your PHI and reducing your liability is key for you business. Using HIPAA compliance tracking software can help you illustrate to auditors that you have done everything necessary to comply with the regulations.
The main focuses of your HIPAA compliance software should include:
- Business Associate Management
- Gap Analysis
- Remediation Management
- Incident Management
- Policy & Procedure creation (Templates)
- Policy & Procedure Management (Version Control)
- Attestation Management (Staff attesting to policies, procedures and training)
Mr. Grant was quoted as saying: “Compliance is no longer a three ringed binder up behind someone’s desk; it needs to be a living, breathing solution that everyone in the organization can access.” He goes on to say “Compliance is ever changing and needs a solution that is updated and flexible to meet the needs of documenting compliance standards. That is very hard to do with a paper system.”