A phishing campaign has been identified that uses fake VPN alerts as a lure to get remote workers to divulge their Office 365 credentials.
Healthcare providers have increased their telehealth services during the COVID-19 public health emergency in an effort to help prevent the spread of COVID-19 and ensure that healthcare services can continue to be provided to patients who are self-isolating at home.
Virtual private networks (VPNs) are used to support telehealth services and provide secure access the network and patient data. Several vulnerabilities have been identified in VPNs which are being exploited by threat actors to gain access to corporate networks to steal sensitive data and deploy malware and ransomware. It is therefore essential for VPN systems to be patched promptly and for VPN clients on employee laptops to be updated. Employees may therefore be used to updating their VPN.
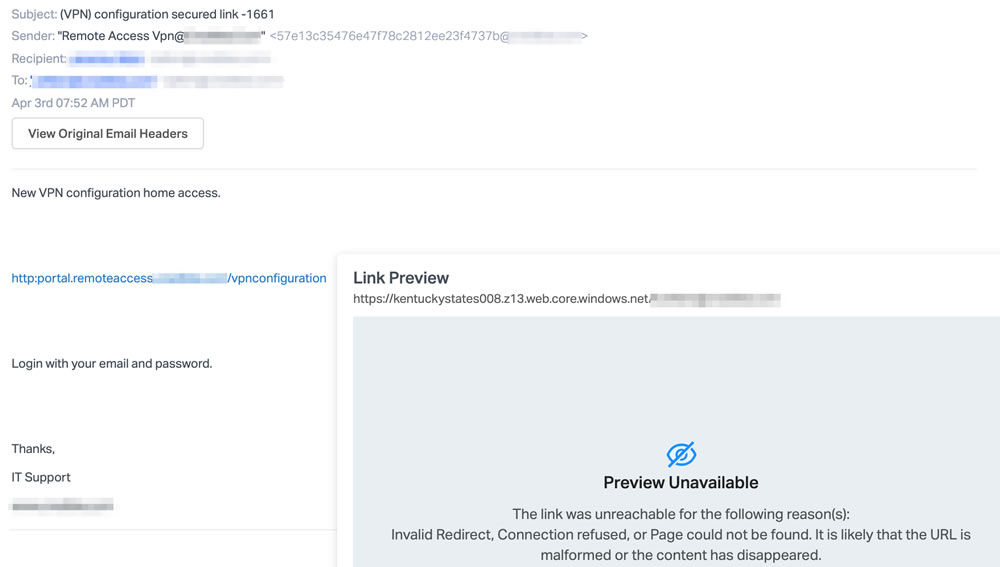
Researchers at Abnormal Security have identified a phishing campaign that impersonates a user’s organization and claims there is a problem with the VPN configuration that must be addressed to allow the user to continue to use the VPN to access the network.
The emails appear to have been sent by the IT Support team and include a hyperlink that must be clicked to install the update. The user is told in the email that they will be required to supply their username and password to login to perform the update.
This campaign targets specific organizations and spoofs an internal email to make it appear that the email has been sent from a trusted domain. The hyperlink has anchor text related to the user’s organization to hide the true destination URL to make it appear legitimate. If the user clicks the hyperlink in the email, they will be directed to a website with a realistic Office 365 login prompt. The phishing webpage is hosted on a legitimate Microsoft .NET platform so has a valid security certificate.
Login credentials entered on the site will be captured by the attacker and can be used to access the individual’s Office 365 email account and obtain sensitive data in emails and attachments, as well as other data accessible using the Office 365 credentials through single sign-on.
Abnormal Security has found a variety of phishing emails that use variations of this message, which have been sent from several different IP addresses. Since the destination phishing URL is the same in each email, it suggests that the emails are part of the same campaign and have been sent by a single attacker.
The post Fake VPN Alerts Used as Lure in Office 365 Credential Phishing Campaign appeared first on HIPAA Journal.